
by rkyadav245833@gmail.com | Nov 6, 2025 | Uncategorized
The recent Gujarat maternity hospital CCTV hacking case exposed a dark truth — most surveillance systems meant to ensure safety are themselves dangerously insecure. Hackers accessed and sold over 50,000 private video clips from hospital and residential CCTV dashboards...

by rkyadav245833@gmail.com | Jul 16, 2025 | Uncategorized
Got it, let’s dive deeper into the technical aspects of PCAP analysis for network-based attacks. From PCAP to RCA: A Technical Deep Dive into Network Attack Storytelling Understanding the intricate details of a network-based attack requires a meticulous...
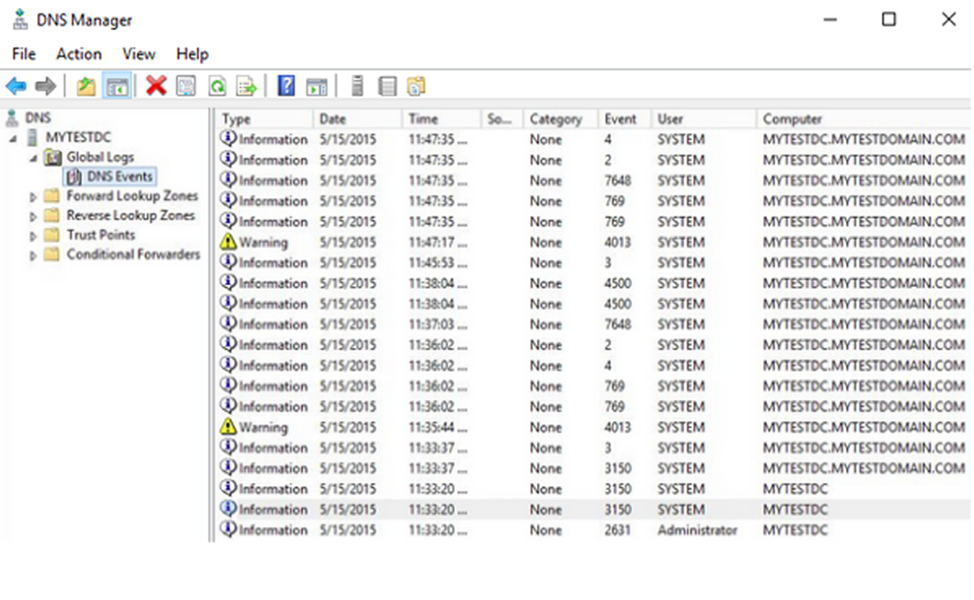
by rkyadav245833@gmail.com | Jul 16, 2025 | Uncategorized
In any Security Operations Center (SOC), Windows Event Logs are one of the most essential and frequently used data sources for threat detection and incident investigation. Whether you’re working in a Tier 1 analyst role or just starting your cybersecurity...

by rkyadav245833@gmail.com | Jul 15, 2025 | Uncategorized
Persistence is a crucial stage in the cyber attack lifecycle. After gaining initial access, adversaries often implant mechanisms that allow them to maintain foothold on a compromised system—surviving reboots, credential resets, or even defensive actions. Detecting...




